Recently, businesses, both local and international, have increasingly become the target of cyberattacks. Attackers are continuously looking for new vulnerabilities, even going as far as to threaten the infrastructure of contact centers. Security awareness in the contact center has never been more critical.
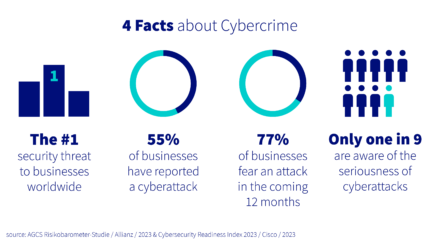
Hackers often shut down entire sections of the affected companies and obtain valuable data simultaneously. Companies from various industries, such as pharmaceuticals, finance, insurance, automotive, transport, and health insurance, have been victims of such attacks. Vulnerabilities often exist within larger IT structures in departments such as customer service. Meanwhile, those who bury their head in the sand or simply try to think security away as an IT issue should heed warning.

Given that security is not an unfamiliar term in IT nowadays, the question arises as to how those in charge of the contact center or customer service infrastructure should deal with it.
Firstly, it is crucial to rethink the business’s security infrastructure and processes. Contact center managers should reframe their thinking and appreciate that they may become victims of a hacker attack and that vigilance is vital to averting threats. These scenarios can seem like pie-in-the-sky thinking to many decision-makers, but it is very real. Having IT infrastructure and applications in the businesses’ IT landscape taken over, having customer data in the grip of criminals, blackmail, extortion, and an overall feeling of powerlessness should naturally be avoided.
Contact centers are an essential interface to the outside world and are, therefore, particularly at risk.

1. Regular software and system performance analysis
Regular reviews and updates of the software and systems in use help identify and address potential vulnerabilities and security gaps before they can be exploited by attackers. Continuous monitoring will help to apply critical security updates and strengthen resilience against attacks.

2. Safety education
Employee training and awareness of cybersecurity practices are essential. A well-informed team can detect suspicious activity, see through attacks, and handle sensitive data more conscientiously. By keeping up to date on current threats and best protection practices, employees can help reduce the organization’s attack surface.

3. Sustained alertness
Maintaining a healthy skepticism toward unexpected emails, messages, or requests can make a significant difference. By remaining vigilant and ensuring all communication is legitimate, threats from phishing attacks and fraudulent activity can be reduced. Recognizing suspicious content helps prevent attackers from having an easy time.
Learn more about security in cloud contact centers.
This is an abridged version of an interview that originally appeared on Teletalk.de in German.